- cross-posted to:
- lobsters
- cross-posted to:
- lobsters
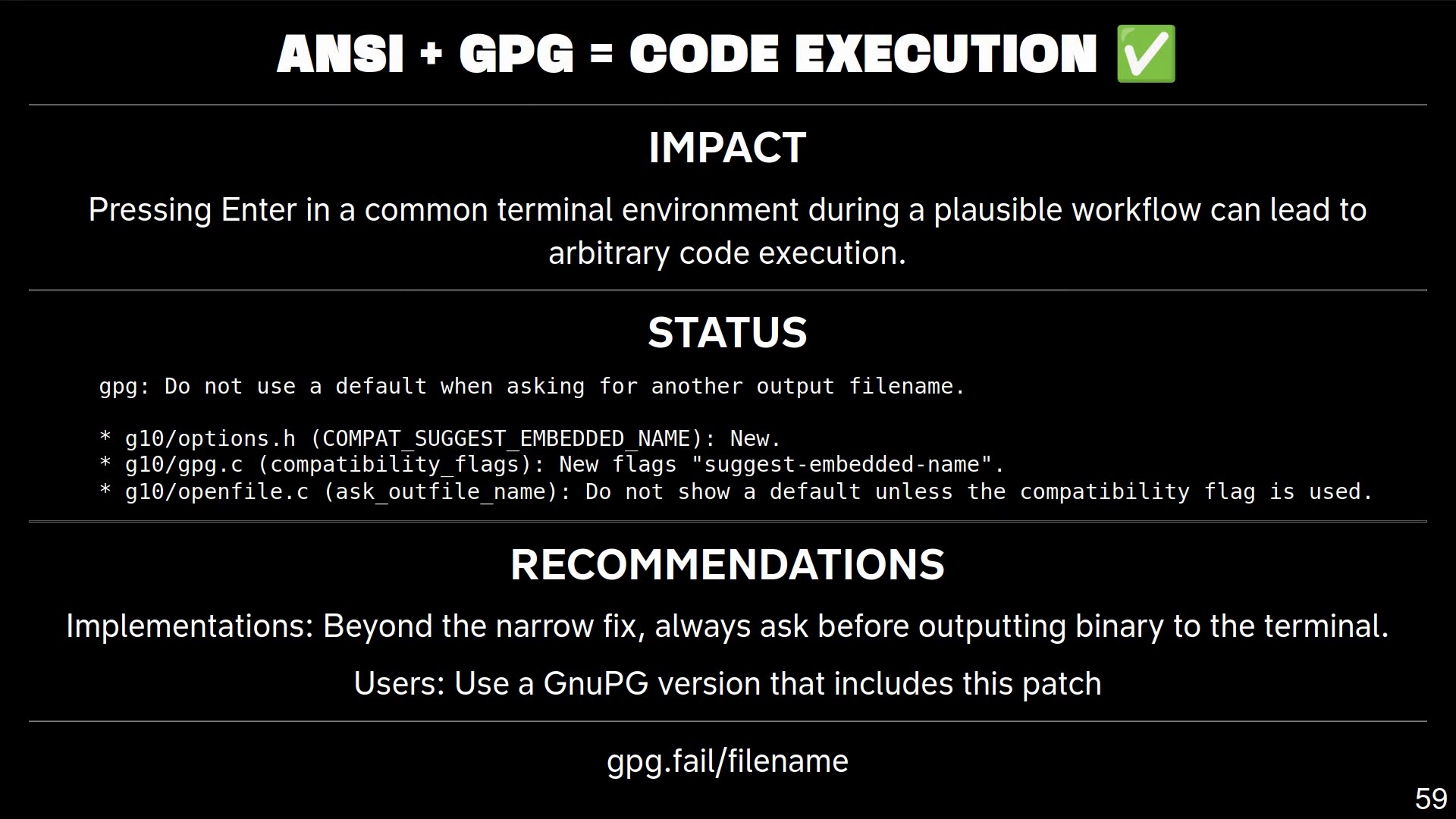
A talk from the hacker conference 39C3 about security vulnerabilities found in GPG (GnuPG) and similar tools.
They showed 14 vulnerabilities (9 of them are 0-days) 🤯.
Their website: https://gpg.fail/
(in English)


What do they suggest for the secure way to validate the header line?
Let’s say it is
Hash: SHA1and then a millionnbspand then a newlineIs the header line now considered invalid because of arbitrary character limit?
Is it invalid because the maximum length of a known hash function is (insert figure here)?
Should the million
nbspbe a part of the text being signed?